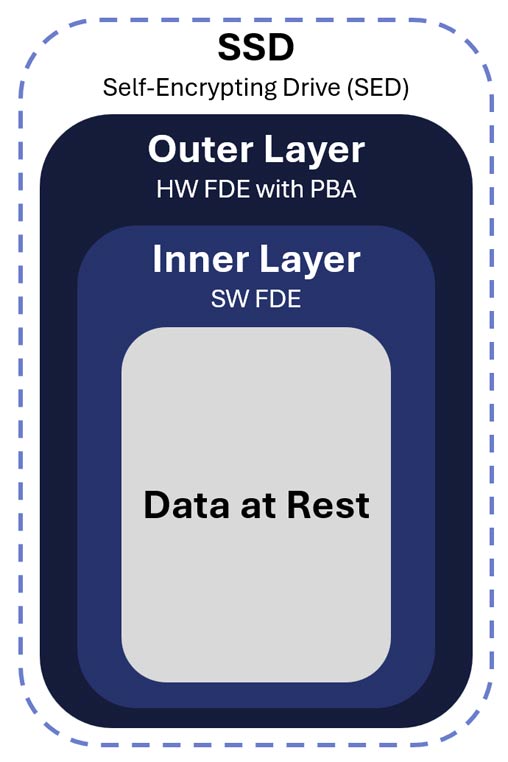
CSfC DAR Outer-Layer Protection
The outer layer requires Hardware Full Drive Encryption (HW FDE) combined with Pre-Boot Authentication to establish the first independent layer of Data at Rest security.
Hardware Full Drive Encryption
What is Hardware FDE?
A Self Encrypting Drive uses hardware-based encryption to secure Data at Rest. This encryption utilizes dedicated physical electronic components (like a specialized chip on a drive or an instruction set built into a CPU) to perform the computationally intensive processes of the Advanced Encryption Standard (AES) 256-bit algorithm. To be listed on the CSfC DAR component list requires meeting extensive standards and completing rigorous testing.
Key capabilities include:
- AES-256 Bit Encryption: Is the current gold standard for protecting sensitive data globally. The AES algorithm was specifically designed to be highly resistant to all known forms of cryptographic attacks and the 256-bit key provides a colossal number of possible combinations (2^256).
- Key Management: The 256-bit encryption key is generated and stored securely within the hardware itself, making it far less vulnerable to extraction through software-based attacks like memory dumps or keyloggers.
- Dedicated Processor: Instead of relying on the host system's main CPU and memory, a separate, dedicated hardware processor or chip handles the encryption and decryption.
- On-the-Fly Processing: Data is encrypted as it's being written to a storage device (like an SSD or USB drive) and decrypted as it's being read, all in real-time.
Pre-Boot Authentication
What is Pre-boot Authenticationt?
Pre-Boot Authentication (PBA) requires the user to authenticate before the operating system begins loading. It runs in a secure, isolated shadow partition.
PBA is an essential component to ensure the effectiveness of hardware encryption. Specifically PBA:
- Prevents Unauthorized Access Before Operating System Loads: Without Pre-Boot Authentication, a computer with full disk encryption might automatically decrypt the drive as the operating system loads (e.g., using only a Trusted Platform Module (TPM) chip). This leaves the data vulnerable to attackers with physical access who could use various software or hardware attacks (like an "Evil Maid" attack or removing the drive and putting it in another computer) to bypass the OS login and extract data. PBA ensures the encryption key is not released and the drive remains locked until the user is verified in the secure pre-boot environment.
- Mitigates Operating System-Level Vulnerabilities: PBA operates outside the main operating system, meaning attackers cannot exploit software vulnerabilities or OS flaws to bypass security and access data. Protection begins at power-on and remains in place until user identity is confirmed.
Why Does the NSA Require PBA?
Without Pre-Boot Authentication (PBA), hardware full disk encryption (HW FDE) leaves data vulnerable to attackers who have physical access to the device. The core vulnerability is the "authentication gap," where the system may automatically decrypt the drive upon boot without requiring specific user verification in a secure environment
Key vulnerabilities include:
- Bypassing the OS Login: The computer is designed to automatically load the operating system once powered on. Without a PBA screen to intercept this process, the hardware "unlocks" the drive using keys stored on the device itself (often via a Trusted Platform Module or a simple internal password), and the OS boots. Once the OS is running, the data is accessible to anyone who can bypass the OS login, which is often easier than breaking the encryption itself.
- Physical Attacks: An attacker with physical control of the device can employ a variety of attacks to access the data:
- Drive Removal: The self-encrypting drive (SED) can be removed from the original machine and connected to an attacker's computer. If the internal authentication mechanism (like a default or common master password used by some vendors) can be bypassed, the data is readable.
- "Hot-Plug" Attacks: Attackers can place the device in a sleep/hibernate state (where the key might be temporarily stored in RAM), physically remove the drive while maintaining power, and then "hot-plug" it into an attacker's machine to access the unlocked data.
- Exploiting Firmware Flaws: Some older or poorly implemented hardware FDE solutions have had firmware vulnerabilities that allowed researchers to bypass encryption entirely, without requiring the user's password.
Without Pre-Boot Authentication, hardware encryption does not provide meaningful protection because the mechanism that ensures the drive remains locked until the user verifies their identity is missing.