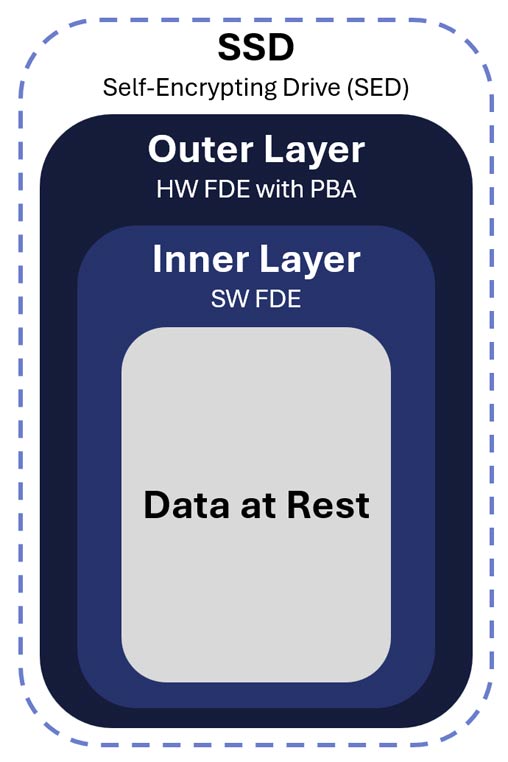
CSfC DAR Inner-Layer Protection
The inner layer requirements mandate the use of Software Full Drive Encryption (SW FDE) to provide an independent layer of Data at Rest (DAR) security.
Software Full Drive Encryption
What is Software FDE?
Software Full Drive Encryption serves as a comprehensive security control that encrypts the entire logical volume of a storage device. All data on the drive, including the operating system, applications, configuration files, and user data, is encrypted whenever the system is powered off or the drive is unauthenticated. As a full-disk solution, Software FDE establishes a complete encryption boundary that protects all stored information.
Once deployed, encryption and decryption take place automatically as data is read or written, allowing users to work normally while the drive remains securely protected. This transparent operation ensures that security is consistently enforced without disrupting workflows or system usability.
Software Full Drive Encryption safeguards sensitive information from shutdown through system boot and operates independently of hardware-based controls. It provides strong Data-at-Rest protection through its own cryptographic implementation. Only NIAP-validated Software FDE solutions can be trusted to use properly validated cryptographic mechanisms and authentication methods, ensuring compliance with CSfC requirements and resilience against sophisticated adversaries.
NSA Software Full Drive Encryption Requirements
Key Software Full Drive Encryption Capabilities
NSA provides strict guidelines for SW FDE to be listed these include:
- Power-off Protection: When the device is powered off, all data on the drive remains encrypted and unreadable.
- Boot Time Enforcement: Upon power-on, the SW FDE requires authentication before the operating system loads, enforcing access control before any data is decrypted.
- Two Factor Access Control: Access to encrypted data may require authentication using both a username/password and a smart card (CAC).
Why Does the NSA Require Two Encryption Layers?
The two layers of protection provide critical redundancy and risk mitigation vs sophisticated nation-state adversaries:
- Mitigate Single Vulnerability: If one of the encryption layers is compromised or fails (due to vulnerability exploitation, misconfiguration, or operator error), the second independent layer can still provide strong encryption to safeguard the classified data.
- Layered Security: Using multiple, independent layers makes the task of an adversary significantly more difficult, as they would have to defeat two distinct cryptographic mechanisms to access the data.
This layered strategy allows government and defense organizations to rapidly field secure systems using modern technology while meeting stringent security requirements.
What is the Manufacturer Diversity?
NSA CSfC manufacturer diversity for DAR builds on the layered security approach, requiring distinct and separate hardware and software encryption solutions. The requirement enhances security by ensuring that a single vulnerability or compromise in one product's code base or supply chain does not compromise the entire solution.
A single manufacturer may provide both layers, subject to strict conditions. The manufacturer must demonstrate "sufficient independence" between the two products, including but not limited to:
- Significant differences in the software code base (e.g., operating system) and cryptographic libraries.
- Differences in cryptographic hardware components.
- Different development teams for each product.
- Measures taken to ensure supply chain risks are no greater than if two different vendors were used.
The NSA reviews all submitted documentation to verify that both layers meet the independence requirements needed for CSfC approval.